Given the sheer size of the target, cloud-based enterprise data is a magnet for malicious security threats from attackers both within and outside of organizations. A single data breach can cost an organization millions — or even billions — of dollars when lost revenue, business interruption, fines, and penalties are taken into account. As cyber attacks and cloud data theft become increasingly common, organizations may wonder who is to blame.
According to a recent Gartner report, the onus is on the cloud user. Gartner predicts that through 2025, a full 99% of all cloud security failures will result from user error. The good news, however, is that these issues are preventable in virtually all cases when the user understands their roles and responsibilities in cloud security.
Understanding Security in the Cloud
Public cloud providers, like Amazon Web Services (AWS) and Microsoft Azure, have no choice but to take their security and compliance responsibilities very seriously. In the early days of cloud, enterprises had initial concerns about the data security in multi-tenant architectures. Security within infrastructures outside of the enterprise’s direct control was also a key consideration. Since then, however, Amazon and Microsoft have assured users that their environments are as secure as on-premises data centers, if not more so.
As a result, we’re seeing an uptick in highly regulated sectors, such as financial services and healthcare, deepening their cloud profiles. Perhaps the strongest endorsement for the security capabilities of today’s leading cloud providers is the CIA’s strategic decision to go all-in on the cloud using a private AWS cloud deployment.
However, Amazon has notably drawn a line in the sand over how far they’ll go to monitor and regulate security and compliance on behalf of their end-users. AWS developed a shared responsibility model, structured in such a way that puts the accountability on customers to close the data security loop in their own environments.
What is the Shared Responsibility Model?
So what is the shared responsibility model? Simply put, the cloud provider is responsible for the security of the cloud, while the customer is responsible for security in the cloud.
Essentially, your cloud provider is responsible for making sure your infrastructure built within its platform is inherently secure and reliable. To provide a secure cloud, the cloud vendor manages and controls the host Operating System (OS) and the virtualization layer. They also guarantee the physical security of the facilities.
On the flip-side, customizable cloud capabilities like application management, network configuration, and encryption are the customer’s responsibility. To ensure security within a given cloud environment, the customer configures and manages the security controls for the guest OS and other apps (including updates and security patches), as well as for the security group firewall. The cloud customer is also responsible for encrypting data in-transit and at-rest.
Approaches to the Shared Responsibility Model in AWS and Azure
In the AWS shared responsibility model, Amazon’s responsibilities fall into two categories. The first is the hardware, which includes all Regions, Availability Zones, and Edge Locations of the AWS global infrastructure. The second category is managing the software for the compute, storage, database, and networking aspects of cloud computing.
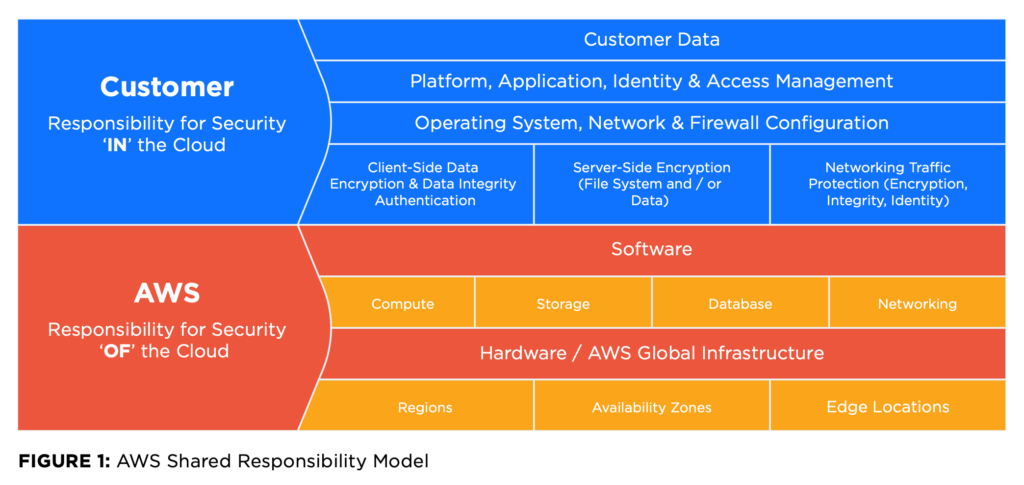
The customer, meanwhile, controls the data and configurations within that cloud environment. In the AWS shared responsibility model, customer responsibility falls into categories such as:
- Customer data stored in the cloud
- Platform, application, and identity & access management
- Operating system, network, and firewall configuration
- Data encryption, integrity, and authentication
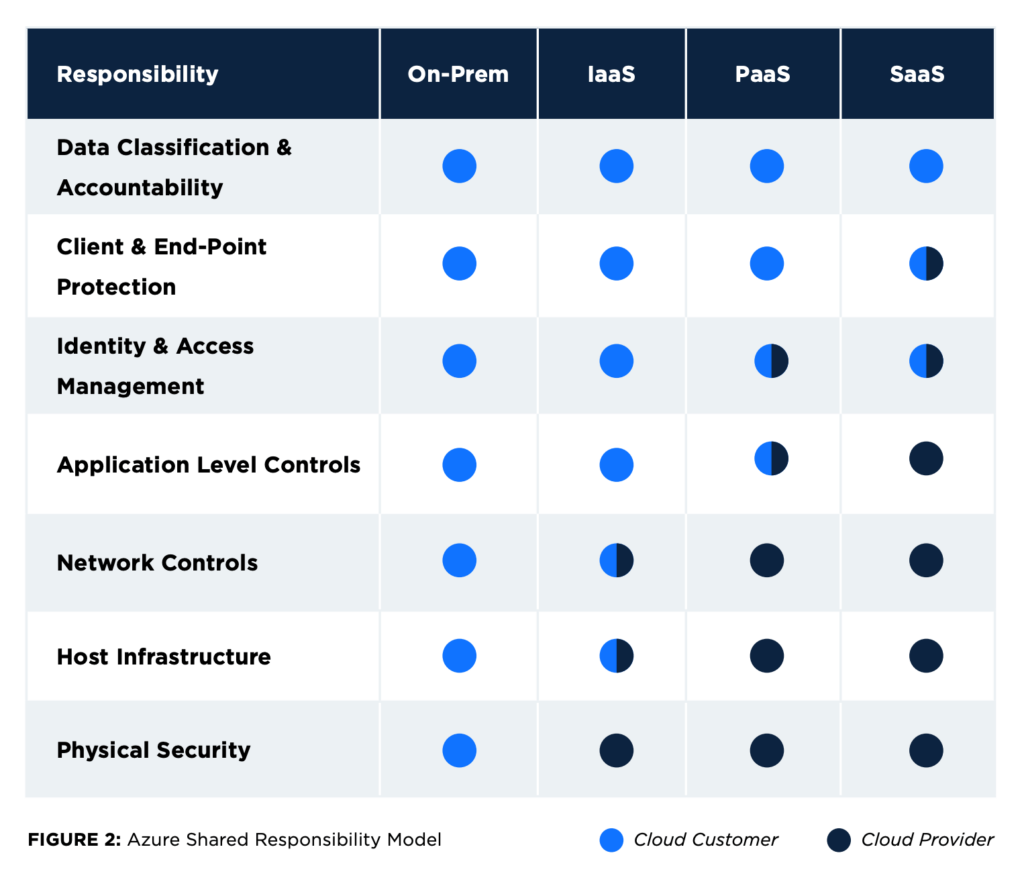
The shared responsibility for cloud security has been adopted by other prominent cloud providers as well. The division of responsibilities in Microsoft Azure’s shared responsibility model differentiates obligations according to the customer’s level of cloud deployment. Those three levels include Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS).
IaaS:
In an IaaS framework, the cloud provider is completely responsible for the physical resources and shares responsibility with the customer for the security of the host infrastructure and network; all the rest is the responsibility of the customer. This level brings the customer the most freedom, but also places the majority of the responsibility in their hands. The principles of IaaS closely follow the shared responsibility model for providers like AWS and Azure.
PaaS:
In a PaaS framework, the provider also takes full responsibility for hosting physical infrastructure and network security, but it also shares responsibility with the customer at the application and access control levels. Application software, virtual machines and instances, and services such as AWS Elastic Beanstalk and AWS Lambda typically fall into the Platform-as-a-Service category.
SaaS:
Finally, in a SaaS framework, the provider takes full responsibility for application controls while sharing responsibility with the customer for access control as well as client/endpoint protection. Generally, SaaS companies provide business applications or other consumer apps over the internet that may run in the cloud, but the term does not apply to cloud providers like AWS, Azure, and Google Cloud.
How to Protect Your Cloud Environment from Security Threats
Organizations in the cloud need to go beyond the basics of merely understanding the shared responsibility model. They also need to make security their first priority. Here are a few best practices that you can follow to enhance the security of your cloud-based assets:
Enforce policies and data governance:
It is entirely the enterprise’s responsibility to put in place and enforce policies for cloud data ownership and responsibility. At the most basic level, the enterprise must understand and classify its data so that the appropriate security measures can be implemented according to the varying levels of data sensitivity.
Diligently manage identity and access controls:
Identity and access management (IAM) in the cloud is substantially more complex than it is in closed, monolithic environments. Cloud providers offer best practice guidelines as well as tools and managed services to help organizations handle IAM, but it’s up to the organization to use them effectively.
Use a cloud management solution:
Next-generation automated cloud monitoring and data security management tools are essential protection as organizations grow their cloud usage. Scaling often increases complexity and dilutes visibility into your cloud environments. A cloud management platform, like CloudCheckr CMx, offers a single dashboard to manage all data, analytics, and users in one place.
CloudCheckr CMx delivers self-healing automation capabilities that can detect and remedy security misconfigurations. CloudCheckr CMx leverages “Fix Now”, “Request Fix”, and “Always Fix” buttons to correct issues as they’re detected—without human intervention. For example, if a user makes an S3 bucket public, automated Best Practice Checks will detect any permissions issues and correct them, and the administrator will be alerted of the correction. Alerts can be enabled to notify appropriate personnel of any specific configuration change via email.
Gain a Deeper Understanding of Your Responsibilities in the Cloud
Cloud providers are constantly investing in innovative solutions to strengthen their security profiles. In order to hold up their end of the shared responsibility model, their customers must do the same. By understanding the shared responsibility model, you can better ensure the security of your cloud infrastructure and improve your overall security posture.
Learn more about how you can protect your cloud environment with CloudCheckr CMx.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter