The clock is ticking on the latest cloud compliance mandate: NIST Special Publication 800-171, otherwise known as DFARS (Defense Federal Acquisition Regulation Supplement). Any organization or contractor that holds or processes unclassified Department of Defense (DoD) data must ensure that they comply with the new DFARS clause.
December 31, 2017 is the ultimate deadline by which to prove compliance, so action is recommended as soon as possible.
As with other compliance mandates, DFARS necessitates ongoing attention. But first, it’s critical that security and DevOps teams understand the requirements of implementing the mandate; anticipating a six- to eight-month ramp up period would be wise. In this article, we’ll share an overview of DFARS, as well as a pragmatic approach to ensuring your organization meets the December deadline.
Implications of DFARS Compliance
In addition to DoD data in your possession, DFARS clause 252.204-7012 will also apply to any subcontractors you may use to fulfill your obligations to the DoD. Failure to be compliant will leave you in breach of contract and subject to criminal, civil, administrative, and contractual actions in law, and equity for penalties, damages, and other appropriate remedies by the United States. It will also leave you open to civil actions for damages and other appropriate remedies by a third party that reports a cyber incident, as a third-party beneficiary of this clause.
Organizations working with the DoD are already used to applying stringent controls to systems that manage classified data, but with DFARS this now extends to unclassified systems that are owned, operated by, or for a contractor and which process, store, or transmit covered defense information. This can have wide-reaching consequences for the contractor who now must extend the security controls across a larger number of systems than in the past.
The DFARS FAQ illustrates the requirements for protecting covered defense information, controlled unclassified information, and Federal contract information when processed or stored on a contractor’s internal information system, or on a DoD system:
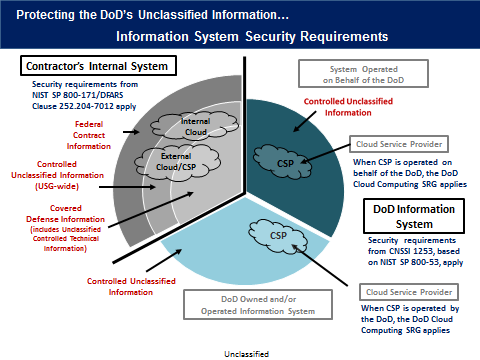
The good news is that the controls specified within DFARS are within normal best practices that any organization should be following, and implementing them will improve the overall security posture of your organization.
Key DFARS Concern
The key areas that DFARS addresses are ensuring adequate security, cyber incident reporting, and subcontracts:
Adequate Security
Adequate security is defined by being compliant with, at a minimum, the following security controls:
For on-premises systems:
For cloud-based systems:
- DoD Cloud Computing Security
- Clause 252.239-7010
- NIST SP 800-171
- Unless you have received written approval from the contracting officer, cloud computing services should be located within the United States or outlying islands
- Ability to support applicable system-wide search and access capabilities for inspections, audits, and investigations
The contractor must also ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline. Additionally, the cloud service provider must comply with requirements in paragraphs (c) through (g) of this clause for cyber incident reporting, malicious software, media preservation and protection, access to additional information and equipment necessary for forensic analysis, and cyber incident damage assessment.
Cyber Incident Reporting
Cyber incidents that impact a system within the scope of DFARS must be reported with 72 hours of detection. To report cyber incidents, you must have a medium assurance certificate.
A review must be conducted so that the scope of the compromise can be understood. At a minimum, this review must cover:
- Identification of affected systems
- Affected users accounts
- Affected data
- Other systems that might have been compromised
The DoD has the right to request further information to enable it to investigate the cyber incident. To this end, the contractor:
- Should take images of affected systems and any relevant monitoring/packet capture data for at least 90 days from the submission of the cyber incident report to allow DoD to request the media or decline interest.
- Provide access to the DoD to allow them to carry out forensic analysis.
- Work with the DoD and provide any additional information that they require to complete the investigation.
Subcontracts
If you subcontract any work that is in scope of the DFARS, you must ensure that your subcontractors are compliant. They, too, must report cyber incidents directly to the DoD and the primary contractor within 72 hours.
Understanding DFARS at Scale
With over 100 security controls to abide by, the DFARS mandate may sound complex—but it doesn’t have to be. CloudCheckr works with advanced technology partners to help organizations achieve compliance and improve their security posture in the cloud. (In fact, CloudCheckr alone helps with 41 of them.) It is important to understand the entirety of DFARS requirements, as well as your current security state, to ensure your organization is compliant by December 31st.
In our next post, we’ll share how your organization can develop a foundation and roadmap for becoming DFARS compliant.
Learn more about our solutions for federal agencies, and reach out to us to discuss how CloudCheckr helps support reaching DFARS compliance, as well as compliance standards driven by NIST 800-53, FedRAMP, HIPAA, and other security requirements.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter
