While Robocalling firms are probably not high on the list of businesses that the public has a lot of sympathy for, such businesses do have access to our personal data, and that deserves protection. Unfortunately, another security breach occurred this week as hundreds of thousands of voter records were exposed on an AWS S3 Bucket operated by Virginia-based RoboCent. The personal information included names, addresses, political affiliations, gender, age, ethnicity, education, and, of course, phone numbers. At a time when the U.S. electoral system is under the microscope, making such information freely accessible to the public, including foreign agents, is disturbing. Considering that such incidents have been widely reported for over a year, businesses should have been taking steps to avoid repeating them.
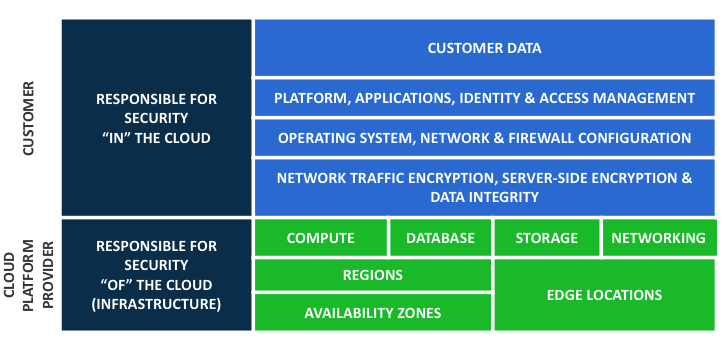
The issue is that AWS as well as Microsoft Azure and all public cloud platforms follow the Shared Responsibility Model. The infrastructure vendor is responsible for “Security OF the Cloud” such as physical security and hardware access while the customer is responsible for “Security IN the Cloud” such as passwords, permissions, encryption and network access control lists. AWS makes S3 Buckets private by default, so whenever such a breach occurs, it is because an operator deliberately chose to make the storage container public, and someone chose to put sensitive data in that container.
In a welcome move, Amazon made their S3 Bucket permissions check free for everyone, not just those who pay extra for AWS Business or Enterprise Support. CloudCheckr has already been giving away S3Checkr.com for free since July, 2017. “It’s in everybody’s interest that the cloud be secure,” noted Adam Kranitz, Director of Marketing at CloudCheckr. “That’s why we made S3Checkr.com free as well as BlobCheckr.com for Azure storage. Sometimes administrators need that extra reminder to lock down their storage, like a reminder to change your smoke alarm batteries.”

While a single check is a good start, what is needed is automated self-healing, as provided by CloudCheckr. Indeed, many of CloudCheckr’s 500+ Best Practice Checks offer “Fix Now” and even “Always Fix” capabilities. This means fixing an S3 bucket’s permissions can be done with the click of a mouse. And with “Always Fix” activated, whenever such a misconfiguration is detected, CloudCheckr can fix it automatically, even while administrators are sleeping.
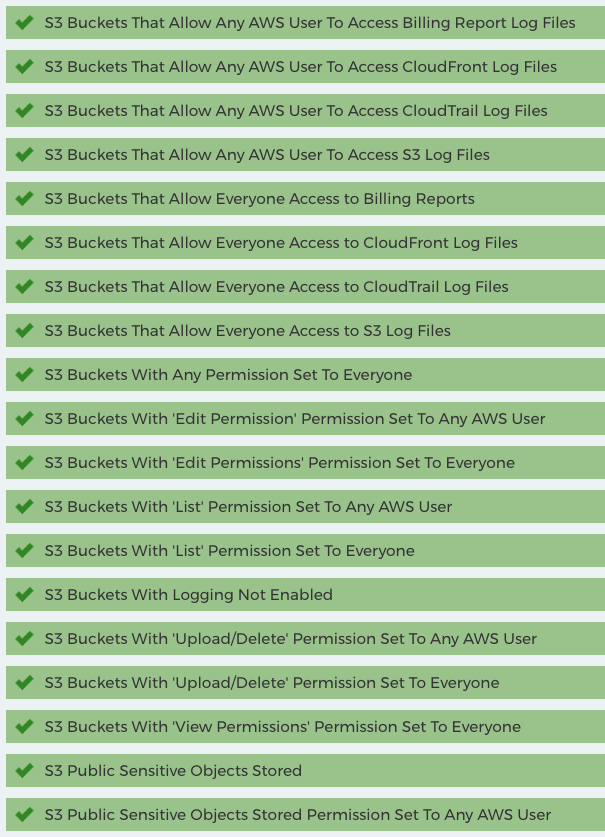
It’s also worth noting that a single check to see if S3 buckets are open to the public is important, but CloudCheckr actually has over twenty checks dedicated to S3 permissions alone. CloudCheckr’s S3 checks include list, edit permissions, upload/delete, read, view permissions and whether the user is an AWS user or the general public. Are you using encryption? CloudCheckr can even check if sensitive data is exposed, looking for keywords such as legal, classified, undisclosed, payroll, HIPAA, audit, invoice, confidential, plus dozens more. Plus, Trusted Advisor is integrated into CloudCheckr so there is no need to check your configuration in two places.
At the end of the day, the Shared Responsibility Model means cloud administrators have to secure everything in their domain. Cloud providers offer the tools admins need to follow best practices, automatically.
Schedule a demo to see how CloudCheckr can help you secure your cloud, or try a 14-day free trial.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter