CloudCheckr + Amazon GuardDuty: Cloud Security You Can Trust
In November, as part of the re:Invent 2017 keynote, Amazon Web Services announced a new hacker intrusion monitoring and detection service: Amazon GuardDuty — an agentless service that can be enabled across all AWS accounts and workloads with a few clicks in the AWS Management Console. In this blog we will explore the features and benefits of Amazon GuardDuty, as well as the advantages of bundling this service with CloudCheckr’s Cloud Management Platform (CMP) that optimizes spend, eliminates waste and improves security and compliance across multi-cloud deployments.
About Amazon GuardDuty
With no upfront cost and no need to install software or security infrastructure, Amazon GuardDuty provides the following benefits:
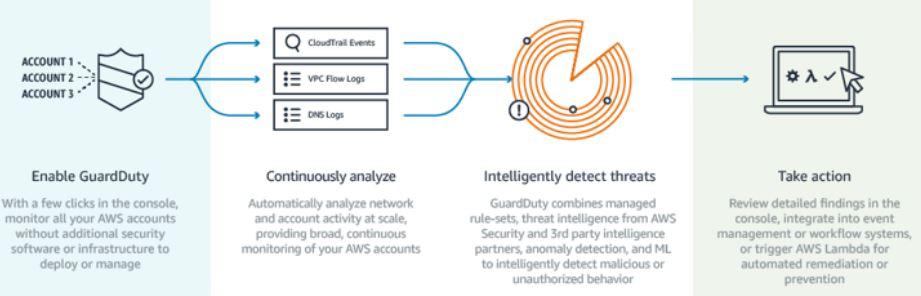
- Near real-time, intelligent threat monitoring, based on the analysis of two input streams:
- Billions of events from AWS CloudTrail (AWS user and API activity), Amazon VPC Flow logs (network traffic data), and DNS Logs (name query patterns).
- Threat intelligence, such as lists of known malicious IP addresses from AWS Security and third-party threat intelligence partners such as CrowdStrike and ProofPoint.
- Centralized threat detection and management across all AWS accounts, giving your security team the single-pane visibility necessary to better manage, prioritize and respond to anomalous account and network activities. The two examples that AWS gives of anomalous activities are remote API calls from a known malicious IP address, and an Amazon EC2 instance sending encoded data within DNS queries.
- Automated threat response via remediation scripts or AWS Lambda functions that are triggered based on GuardDuty security findings, which include details about the affected resource(s) (such as tags, security groups, credentials) as well as information on the attacker (such as IP address and geo-location). In the example provided by AWS, GuardDuty will alert you if an instance is suspected of having data stolen, in response to which you can automatically restrict outbound access for that instance.
The following schematic summarizes how Amazon GuardDuty works:
As noted, there are no upfront costs for the GuardDuty service. After a 30-day free trial, users pay only for the events analyzed, as follows:
- AWS CloudTrail analysis: $4.00 per 1,000,000 events
- VPC Flow Log + DNS Query Log Analysis:
- First 500 GB/month = $1.00/GB
- Next 2,000 GB/month = $0.50/GB
- Over 2,500 GB/month = $0.25/GB
GuardDuty Combined with CloudCheckr
As an AWS partner, CloudCheckr believes that GuardDuty provides an important link in the cloud security chain. However, the ideal solution is to avoid hacks in the first place by using CloudCheckr, adhering to our Best Practice checklist, and staying compliant with the leading security standards.
With both CloudCheckr’s CMP and Amazon GuardDuty in place, AWS users can rest easier knowing that most hack attempts will be thwarted by CloudCheckr before they become bona fide threats. Additionally, Amazon GuardDuty will provide another important level of protection should some of those attempts succeed in compromising their AWS accounts or instances.
CloudCheckr and Amazon GuardDuty make an ideal pair for protecting against security intrusions and detection, without the overhead associated with an agent.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter