Public Cloud Security Precautions Every Business Should Take Seriously
Key Takeaways:
- More businesses are adopting cloud to give remote employees 24/7 access to crucial information
- Organizations in highly regulated industries must ensure that their applications comply with various security requirements to protect sensitive data
- A cloud management platform can assist information security teams in preventing and mitigating threats to data stored in and accessed through cloud services
“Social distancing” may be the new term we’ve adopted to describe our lives in public. However, we’re not only keeping physical distance between us. More and more, the data that powers our work and play (hello, Netflix binge-watching!) is shifting to the cloud instead of being stored in on-premises servers.
With remote teams connecting from all over the world, businesses no longer need a single, physical location for workers or data to reside. With public cloud platforms, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud, personnel can access crucial data from anywhere and at any time. To meet current work-from-home demands, access to the cloud can be scaled up or down depending on usage. For instance, with more reliance on remote work for the foreseeable future, companies can increase their cloud capabilities and continue business as usual in this unusual time.
In a mid-March 2020 survey from brokerage firm Instinet, 68% of CIOs said that cloud services would become more of a priority for their businesses.
Research points to increasing public cloud adoption over the next year, even amid—or perhaps as the result of—the current COVID-19 pandemic and widespread economic interruptions. In a mid-March 2020 survey from brokerage firm Instinet, 68% of CIOs said that cloud services would become more of a priority for their businesses. Respondents also reported a projected reduction in on-premises workloads, from 59% relying on on-prem assets in 2019 to an estimated 35% by 2021.
Cloud services have made the transition to working remotely simpler for many businesses. Yet with more remote workers accessing these resources, IT administrators and cybersecurity teams need to prioritize public cloud security and compliance. In the Instinet survey, 86% of CIO respondents said that cloud security was now a higher budget priority. How can businesses protect their investment in public cloud?
Highly regulated industries in the cloud
The first step for businesses is recognizing where they need to achieve compliance and increase security efforts. Security and compliance regulations can vary depending upon industry, and they can be especially strict when it comes to cloud computing. In highly regulated industries, non-compliance can result in fines, penalties, and other consequences for a business.
Telehealth providers must stay compliant with the HIPAA Security Rule when conferencing with patients and handling electronic Protected Health Information (ePHI).
Regulatory industries have begun modernizing to enable workers to connect with colleagues and clients remotely. Emerging video conferencing applications, such as Zoom, Skype for Business, and Cisco, enable employees to hold meetings and interact with clients in any location. Just as financial information, patient health history, and other records need to stay secure and confidential, so does the video and audio data being streamed and transmitted among remote workers and their customers.
For instance, telehealth providers must stay compliant with the HIPAA Security Rule when conferencing with patients and handling electronic Protected Health Information (ePHI). The ways in which patient data is stored and broadcast via telemedicine applications, and who can access that data, are all highly regulated. HIPAA Security Rule guidelines stipulate the protection of ePHI through a system of secure communication and a system that monitors communications containing ePHI to prevent accidental or malicious breaches. Additionally, only authorized users should have access to this sensitive information. While cloud storage is an effective way to manage this data, healthcare organizations need to ensure that the data is secure and audit-ready at all times. Oftentimes, these institutions can’t guarantee that their data is safe using native public cloud tools alone.
Federal agencies are also relying on remote access to data right now. They have to comply with FedRAMP compliance, a standardized program for security assessment, authorization, and monitoring for cloud services. Many state governments are undergoing similar transitions from on-prem to cloud data storage. Other highly regulated industries like financial services, education institutions, and telecommunications providers all have their own standards that they must meet in order to protect sensitive customer data.
Top public cloud security challenges
While public cloud services provide businesses and agencies with effective data storage, access, and management, they are not an “out-of-the-box” solution. What many organizations fail to understand—sometimes too late—is that these platforms alone are often insufficient when it comes to offering total data protection.
Many cloud services adhere to a shared responsibility model. This means that while the cloud provider protects the security of the cloud as a whole, the customer must protect the security of their data within the cloud. In other words, the user must ensure the integrity of client data, identity and access management, encryption, and other components of their cloud architecture.
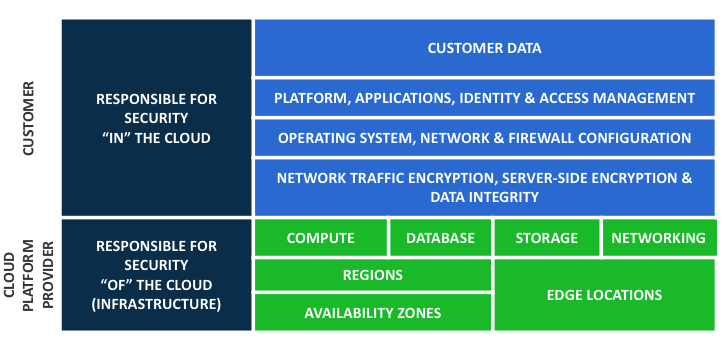
As more organizations migrate to the cloud, they must prioritize their security strategies. They may believe that native tools are enough to rely on, but in truth they need to look further for comprehensive cloud security.
In a recent report, the Cloud Security Alliance (CSA) outlined the top 11 threats to cloud computing for 2020. Data breaches, misconfiguration and inadequate change control, a lack of cloud security architecture and strategy, and insufficient identity and access management were among the biggest security challenges for all industries operating in the cloud. These issues are not unique to any particular industry, but fortunately, they have common solutions.
1. Preventing data breaches
The challenge:
A data breach can involve the release and/or theft of “personal health information, financial information, personally identifiable information (PII), trade secrets and intellectual property,” said the CSA report. The consequences of compromised data can include fines and other legal penalties, lost customers, and even the closure of a business.
The solution:
Being proactive will help businesses and agencies identify threats before they lead to catastrophic losses. A cloud management platform can provide continual monitoring through automation, so that information security teams receive alerts the moment an anomaly occurs instead of discovering compromised data months—or years—later.
2. Correcting misconfiguration and inadequate change control
The challenge:
Misconfiguration of public cloud resources is the leading cause of data breaches, said the CSA report. Common examples of this misconfiguration include unsecured data storage elements or containers, excessive permissions, credentials left in default settings, or other control features that are improperly set up or altogether disabled.
The solution:
Again, cloud management platforms can fill in security gaps and work to correct errors. “Companies should embrace automation,” said the CSA report, “and employ technologies that scan continuously for misconfigured resources and remediate problems in real-time.” With these tools, administrators can review AWS config and other rules to ensure they meet audit requirements at all times.
3. Building a cloud security architecture and strategy
The challenge:
Moving to the cloud is more than a “lift-and-shift” effort when it comes to security said the CSA report. What worked for on-prem assets will likely not work in the cloud.
The solution:
Information security executives should develop clear security strategies that align with business objectives and ensure that their threat models are up to date. The CSA recommends that security strategies include continuous monitoring for vulnerabilities. Automating these processes with a cloud management platform can take the place of time-consuming manual work and eliminate vulnerabilities with the push of a button.
4. Managing sufficient identity, credential, access, and key policies
The challenge:
Identity and access management enables organizations to manage, monitor, and secure access to valuable data and resources. Security incidents can arise when administrators ignore best practices like multi-factor authentication; regular automated rotation of cryptographic keys, passwords, and certificates; use of strong passwords; and other measures to protect user credentials.
The solution:
Administrators must develop granular identity and access management policies to give the right people the correct level of access to sensitive data. They can achieve this by using a tool that helps them track users and permissions. Reviewing these policies can also minimize insider threats to data, number six on the CSA’s list of 2020 cloud security challenges.
The move to the cloud is vital in providing personnel with continuous, reliable access to data, whether they are in the office or working remotely. To protect their assets, companies should look to third-party tools to remediate vulnerabilities and ensure that they are following best practices in compliance and security.
Protecting public cloud assets
Stay-at-home orders have pushed many businesses to see remote work as a necessity, not just a “nice-to-have.” Cloud adoption is an essential step in adapting to changes in the way we work.
Organizations already using the cloud could be poised for success in the current situation. “We have theorized the crisis could accelerate the cloud migration,” Instinet said in its report. “We expect firms with public cloud exposure will emerge stronger from the crisis.”
However, companies need more than what native cloud platform tools can offer. Cloud management platforms can help reduce the burden of manually governing complex cloud infrastructures and offer greater security and compliance measures.
CloudCheckr recently introduced CloudCheckr CMx, their next-generation cloud management featuring a new experience for delivering total visibility into infrastructures and organizational management—by individuals, teams, and roles. The CloudCheckr CMx family, including CMx Federal, achieves significant cost savings while ensuring the highest level of public cloud security and compliance for regulated industries, including large enterprises, managed service providers, and government agencies.
With CloudCheckr CMx, you can:
Maintain the highest levels of public cloud security
CloudCheckr CMx is built to the highest levels of security and supports rigorous controls from NIST 800-53. CMx gives highly regulated industries peace of mind through hundreds of security and compliance best practice checks.
Achieve total compliance
CloudCheckr CMx helps organizations ensure that their cloud infrastructure is audit-ready for 35 regulatory standards, including HIPAA, NIST, NERC, and more. Additionally, government agencies can achieve FedRAMP readiness with CloudCheckr CMx Federal, which offers quick fixes for more than 600 security and compliance best practice checks.
Improve productivity through automation
The need for remote access for employees has had businesses scrambling to ensure a relatively seamless transition to this new normal. CloudCheckr CMx brings businesses self-healing automation that identifies and fixes security and compliance issues. This helps information security personnel take the guesswork out of managing the cloud and frees up those resources to handle other, more immediate tasks as their colleagues adjust to remote work.
See CloudCheckr CMx in Action
Discover why the largest enterprises, service providers, resellers, and government agencies trust CloudCheckr. Request a live 30-minute demo or sign up for a free trial today.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter
