Building a Secure Public Sector Cloud with the Center for Internet Security
The Center for Internet Security, known as CIS, is a US-based nonprofit organization dedicated to making cybersecurity best practice common practice. CIS members include large corporations, government agencies, major universities, and national and international professional organizations. It’s been around since 2000, when it was founded by a group of organizations focused on IT security and governance, including the ISACA, the American Institute of Certified Public Accountants (the creator of the System and Organization Controls (SOC) cybersecurity framework), and the Institute of Internal Auditors.
The CIS mission is to identify, develop, validate, promote, and sustain best practice solutions for cyber defense, as well as to build and lead communities to enable an environment of trust in cyberspace. To that end, CIS provides free resources for security best practices as well as memberships, consulting, and other services to help both private and public sector organizations improve cybersecurity in the cloud and throughout their overall IT infrastructure.
CIS’s Role in Cybersecurity in the Cloud
Perhaps the foundation of CIS’s role in preventing cyberattacks is the CIS Controls, a best practice checklist and cyber defense framework that guides organizations on how to secure their digital infrastructures.
CIS Controls
The CIS Controls are a set of 20 critical security controls or key actions organizations should take to improve cyber defense. Generally speaking, the CIS Controls are meant to provide actionable advice to security teams in both the private and the public sector. The CIS Controls are designed to be implemented and monitored using automation tools—in fact, one of the overarching principles in designing the CIS Controls was to encourage the use of automation to enforce security best practices in an effort to reduce or eliminate the possibility of human error.
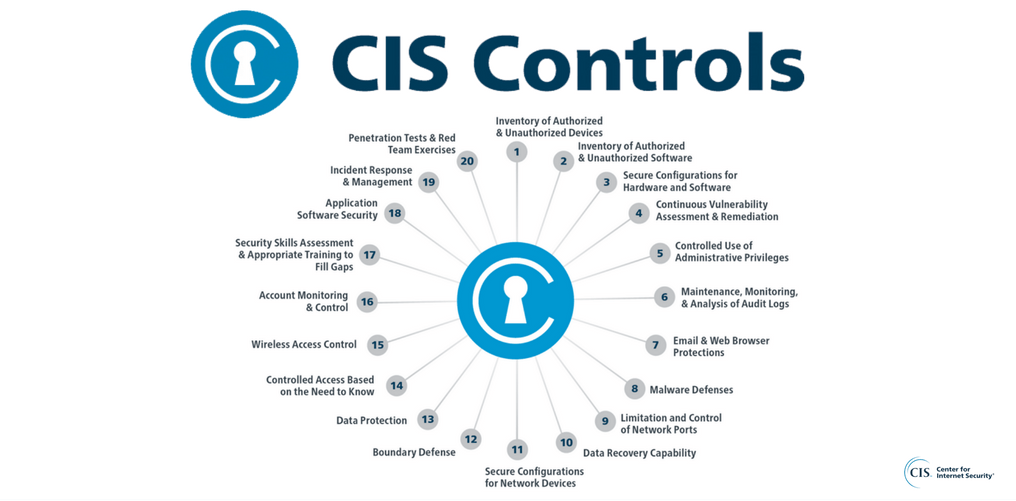
The 20 CIS Controls are cross-cut into three Implementation Groups based on an organization’s unique risks and resources. Implementation Group 1 includes the most essential security actions for organizations with limited cybersecurity resources, while Implementation Groups 2 and 3 cover more advanced techniques. The CIS Controls are updated annually through a consensus-development process involving subject matter experts, private sector companies, government agencies, and community volunteers.
Many of the government agencies who participate in the creation of the CIS Controls every year are very security conscious. They include the National Security Agency, the Department of Homeland Security, and the Department of Defense.
Does it work? According to a 2018 testimony by CIS Chief Executive Officer John Gilligan to the Department of State, the CIS Controls were assessed as preventing up to 90% of pervasive and dangerous cyber-attacks. This is because security breaches are auto-detected when release, change, and configuration management controls are implemented.
CIS Benchmarks
In addition to the CIS Controls, CIS also offers CIS Benchmarks, which are security configuration guidelines. Developed through a unique consensus-based process, the CIS Benchmarks are available publicly and cover a wide variety of technologies. They are also accepted and recognized by the private and public sector, academia, and regulatory compliance organizations. Not only do the benchmarks contain recommendations to securely configure a target system, they also include mappings of the recommendations to the CIS Controls. These mappings help to provide a more comprehensive view into the implementation of both cyber defense and secure configurations. The CIS Benchmarks are a great resource to leverage when looking to securely configure a target system.
CIS has several tools to help organizations assess risk and measure implementation of the CIS Controls, including CIS RAM (Risk Assessment Method). CIS CSAT (CIS Controls Self Assessment Tool), CIS-CAT Pro, and CIS-CAT Lite.
Multi-State Information Share and Analysis Center (MS-ISAC)
Specific to U.S. State, Local, Tribal, and Territorial (SLTT) entities, CIS also operates the MS-ISAC, a “round-the-clock cyber threat monitoring and migration center for state and local governments.” This program was originally designed by the Department of Homeland Security as a resource for state and local governments. All 50 U.S. states are members of the MS-ISAC, as are many local, regional and tribal governments. This program allows for better information sharing between government agencies and law enforcement about cyber threats, as well as promote awareness in public sector organizations about the steps needed to ensure secure IT environments.
Taking the Next Steps in Cybersecurity with CloudCheckr
Using CloudCheckr for compliance monitoring and cybersecurity in the cloud is exactly in line with the CIS recommendation to use automation tools for as many security processes as possible. Human error is one of the biggest causes of security vulnerabilities, whether it is misconfigured permissions or an S3 bucket mistakenly made public. In real life, the kind of comprehensive monitoring necessary to achieve continuous security isn’t possible without automating the monitoring and enabling auto-healing of obvious security vulnerabilities.
CloudCheckr has capabilities to help public sector organizations take their security and compliance a step further than required to meet CIS requirements, with CloudCheckr Total Compliance dashboard and SnapBack.
Total Compliance
The CIS Controls are important standards to meet, especially for public sector organizations in the United States. But they are far from the only compliance framework out there. CloudCheckr Total Compliance monitors cloud infrastructure for compliance with 35 different regulatory standards. The CIS Controls are just one of the 35 standards CloudCheckr monitors.
Adding compliance checks for standards like the AICPA SOC2, HIPAA and FISMA ensure that the organization’s infrastructure is as secure as possible, by any and all standards. It also gives public sector IT administrators the peace of mind that they can handle any kind of sensitive information securely.
SnapBack
Handling data responsibly is crucial, but in the context of a compliance audit, it’s also important to maintain records of continuous compliance. Without a way to record how the cloud infrastructure has maintained security in the past—whether one day ago or three years ago—accessing the information needed in an audit can be impossible. With CloudCheckr SnapBack, organizations can completely automate this data collection and retention. Compliance and security records for up to seven years is collected automatically and available inside the CloudCheckr application. Preparing for an audit of any kind is stressful, but with SnapBack, gathering the data you need is effortless.
The CIS Controls are an important starting point for public sector organizations needing to increase their compliance and cybersecurity in the cloud. Just ensuring that the CIS Controls are met will likely improve security dramatically. Using CloudCheckr to automate security procedures and enable self-healing can be part of the strategy to successfully implement the CIS Controls, but the benefits from CloudCheckr extend beyond its ability to automate permissions and monitor for leaky buckets. Using CloudCheckr can ease the burden of compliance with dozens of regulations and frameworks. In addition, CloudCheckr makes accurate compliance data easily available, reducing the stress related to audits and ensuring audit results are based on accurate information.
Meet CIS Requirements and Improve Your Cybersecurity in the Cloud
Learn how your organization can benefit from cloud management solutions. Try CloudCheckr free for 14 days.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter
