Despite the numerous safeguards built-in to Amazon Web Services (AWS) and the widespread publicity of the S3 breach from a few weeks ago, it has happened again. This time it was the World Wrestling Entertainment organization.
As before, the WWE did not do their part to lock down the data. And the shame of it is, AWS makes it so easy to keep your data secure. In fact, S3 data is protected by default. An administrator would have to explicitly change permissions from private to public, and that is what happened in each case.
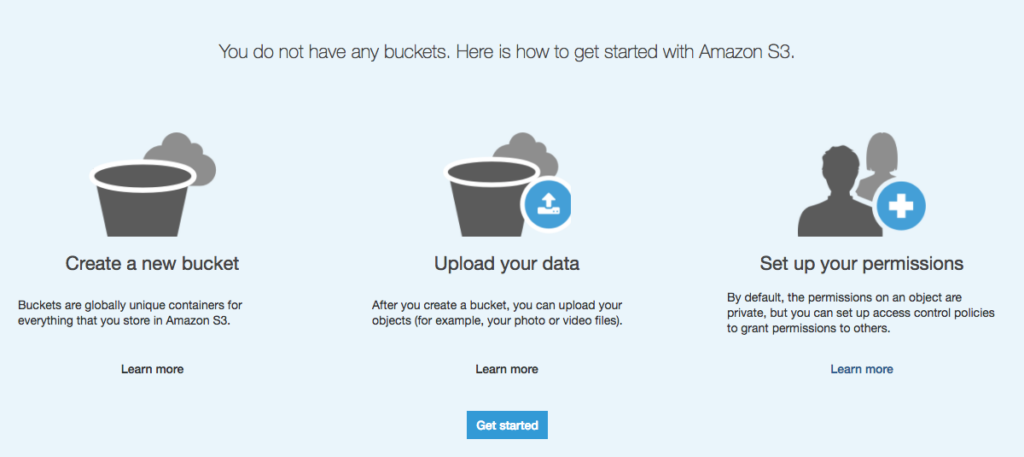
Figure 1: When creating an S3 bucket, “by default, the permission on an object are private,” with AWS.
AWS uses a Shared Responsibility Model and provides plenty of mechanisms to lock down data—but AWS customers must take advantage of those tools. This is similar to a contractor building a secure door, but the homeowner deliberately leaving the door unlocked.
Organizations can avoid such issues by sticking with the default AWS security settings and only enabling S3 bucket access when truly needed. For added security, administrators can also encrypt data, which was not done in these cases. Again, AWS provides all the tools necessary and even offers free training videos to master them.
To help organizations stay safe and secure, CloudCheckr has turned one of our 450+ Best Practice Checks into a free, publicly accessible tool: Try our S3 Permission Checking Tool to ensure your buckets are secure. You do not need to be a CloudCheckr customer to use the tool.
Security researchers as well as hackers try to detect accessible cloud storage using Brute Force techniques, essentially using the power of a computer to guess all possible combinations of a drive’s web address. Enterprises cannot rely on security through obscurity.
The WWE breach was detected by Kromtech Security Research Center, and the data was locked down the data within hours, showing how easy AWS makes it to be secure, as long as you follow best practices. CloudCheckr includes over 450 Best Practices to detect and even automatically fix such misconfigurations thanks to Self-Healing capabilities.
Sign up for a free, 14-day trial of CloudCheckr to see more ways our comprehensive cloud management platform can help keep your cloud safe.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter