Establishing a Secure Public Cloud Architecture With Processes and Best Practices
In the past, the main concern about migration to and running your business in the cloud was the question of whether your data would be secure. As migration to the cloud became more prevalent, our trust in the safety of the public cloud increased. However, many people are still unsure about whether their data is safe in the cloud, and they consider on-premises data centers to be safer places for data storage. Unfortunately, this lack of faith in the public cloud is common.
The security of your data and applications—whether they are stored in the public cloud or an on-premises data center—mostly depends on you. It is worth noting that the task of securing your architecture is much easier inside a public cloud because your cloud provider is responsible for the security of the cloud while your responsibility is security within the cloud. Sharing the responsibility of security is known as the shared responsibility model, and it is the basic principle of security in the cloud.
With on-premises data centers, security issues are resolved by obtaining processes and tools for securing your infrastructure. Additionally, your data and application were on your servers, so you were responsible for network infrastructure and you had physical access to your devices. This method is more static and physical than the cloud. In the cloud, your infrastructure can scale up and down depending on your needs and you can share the host of your application with other users, which means that many tools you previously used for security need to be modified to function within the cloud. The methods may have changed, but the goal of ensuring a secure public cloud architecture remains the same.
Your Responsibilities in the Public Cloud
The shared responsibility model relies on the cloud provider to take care of infrastructure, services, and their security, while you are expected to ensure the security of your own operating systems, platforms, and data. To ensure a secure infrastructure, the cloud provider configures infrastructure components and makes different services and features available to you. Once the provider has done this, you further enhance the security from your end.
With Amazon Web Services (AWS), your first step is to decide which users are granted access and what their permissions to AWS services are. To do this, you will use the Identity and Access Management (IAM) service, which will help you manage users and permissions inside the AWS cloud. Inside the Azure and Google clouds, you need to use Azure Active Directory and Cloud IAM as an equivalent.
A variety of services are available to you within the public cloud, including infrastructure services, container services, and abstracted services. To ensure the security of all of these services, each group has a shared responsibility model. Keep in mind, using some of these services for full security will result in greater responsibility for you, while using others will leave the cloud provider with more responsibility.
Let’s take virtual machines in the cloud (i.e., EC2 instances) as an example, from the infrastructure services category. If you want to make your data on the EC2 instance safe, AWS will be in charge of the security facilities, physical security of the hardware, network infrastructure, and virtualization infrastructure. However, you will be responsible for Amazon Machine Images (AMIs), operating system updates and firewall rules, applications, data in transit, data at rest, data stores, credentials, policies, and configuration.
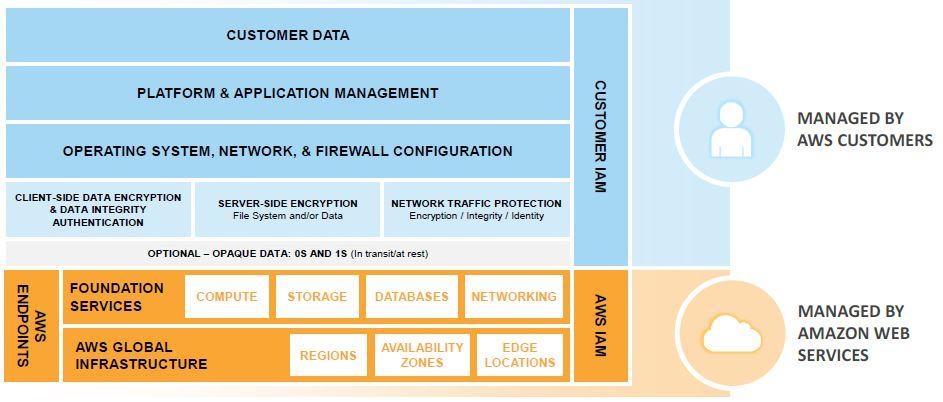
With the container services category, sometimes you cannot access and manage the operating system on the platform layer, so the responsibility for the operating system, updates, and security patches is the responsibility of the cloud provider. Examples of such services are Amazon RDS, Azure SQL Database, and Google Cloud Spanner.
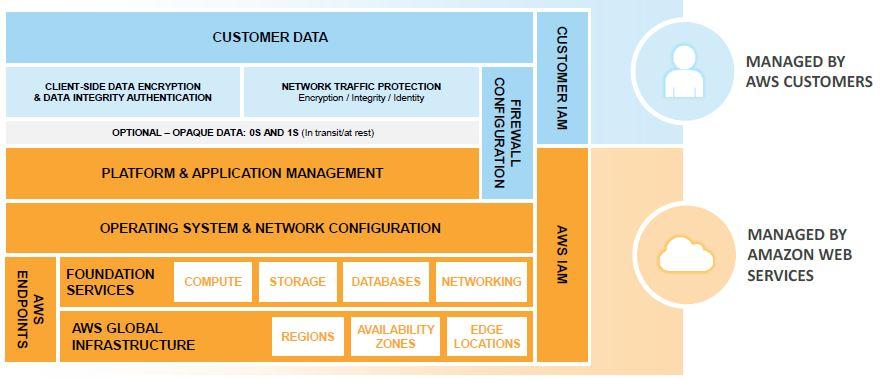
In the abstracted services category, we have high-level storage, database, and messaging services. These services abstract the platform or management layer in which you can build and operate cloud applications. You can access the endpoints of these abstracted services using APIs and then manage the underlying service components or the operating system that they are on.
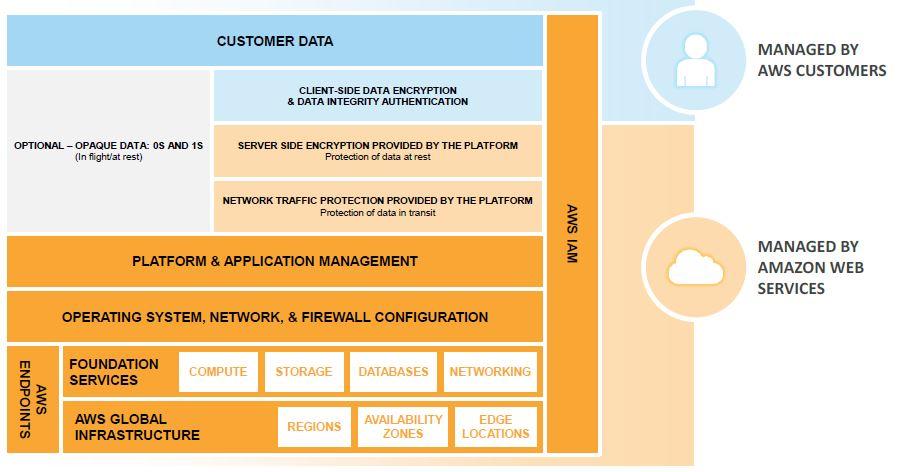
In order to ensure secure architecture in your part of the shared responsibility model, you will need to use the security services given by the cloud provider. One of the first things you should do is access the account of your cloud provider using MFA authentication and follow the principle of least privilege for your users.
Security Best Practices and Security Checklists
There are many best practices to take into account when it comes to building a secure public cloud architecture. A few of these include:
- Identity and Access Management
- Detective controls
- Infrastructure protection
- Data protection
- Incident response
Before you create architecture for any system in the cloud, you need to set up a security process. You need to be able to control who performs which functions, identify security incidents, protect your systems and services, and maintain the confidentiality and integrity of data through data protection. It is necessary to have a well-defined and well-tested process ready to go in case of a security incident. Taking these steps will help you avoid financial losses and prevent you from breaking compliance rules.
As we already mentioned, IAM is a key factor when it comes to security as it ensures that only authorized and authenticated users have access to your resources inside the cloud. To register and identify potential security incidents, you can use detective control, which includes audit and automated alerting based on previously defined conditions. Infrastructure protection includes control methodologies such as in-depth defense and multi-factor authentication, which are necessary to meet best practices and industry or regulatory obligations.
Preventing and Monitoring Security Risks and Vulnerabilities
Even though cloud providers will not allow penetration testing, port scanning, and similar checks without their permission, you should test the vulnerability of your own infrastructure. One of the ways to find and fix vulnerabilities is to create an image of your workflow and test it inside your test environment with the approval of your cloud provider. This is the proactive thing to do.
Patching in the cloud is much easier than it is in on-premises data centers since you have the ability to apply one template on the entire infrastructure with just a few mouse clicks. Monitoring and reviewing your logs will also give you insight into the security of your architecture, and based on that knowledge, you can act preemptively and avoid undesirable consequences.
Inside the AWS cloud, there are several services that can help you with these aforementioned tasks: AWS CloudTrail records AWS API calls, AWS Config provides a detailed inventory of your AWS resources and configuration, and Amazon CloudWatch monitors service of AWS resources. If you use Azure or Google Cloud, you can use the following services: Azure Operational Insights, Azure Application Insights, Cloud Console, Stackdriver Monitoring, and Stackdriver Logging.
Ease the Burden on Your Team With Governance and Automation Tools
It is common to use third-party tools to ensure governance of the entire cloud. Some of these tools are recognized with specific AWS Security Competency status, and they have a long and proven track record of success in the cloud. To stay in compliance with standards, you must meet certain security requirements, so choosing a cloud management tool is helpful for validation.
CloudCheckr is an infrastructure governance platform that enables unified governance of your cloud across your entire cloud ecosystem, and gives you insights for easier management of your security and compliance. CloudCheckr also helps you cut costs and continuously monitor cloud best practices in multi-cloud environments with AWS, Azure and Google Cloud Platform. Additionally, CloudCheckr provides you with automated reports and alerts that can help you identify vulnerabilities and security risks.
While it’s clear that our data is indeed safe in the cloud, the industry should continue to develop safety measures to make it even safer and less vulnerable to attacks in the future. Data is the most valuable resource your company has, so the safety of your—and your customers’—data is extremely important. The process of securing your architecture is not something you will do one time: it is an ongoing process that results in continuous improvements. Cloud providers publish new features and services every day to help us make our data more secure. It is up to you to stay up-to-date and use these services to improve your architecture security. With the constant threat of security breaches, it is critical that you monitor vigilantly and respond proactively to potential threats by monitoring actively.
Ready to make CloudCheckr part of your secure public cloud architecture?
Get a free Cloud Check Up to learn how CloudCheckr can help you address security concerns for your business.
Cloud Resources Delivered
Get free cloud resources delivered to your inbox. Sign up for our newsletter.
Cloud Resources Delivered
Subscribe to our newsletter
